A hacker has published today a list of plaintext usernames and passwords, along with IP addresses for more than 900 Pulse Secure VPN enterprise servers
ZDNet, which obtained a copy of this list with the help of threat intelligence firm KELA, verified its authenticity with multiple sources in the cyber-security community.
According to a review, the list includes:
• IP addresses of Pulse Secure VPN servers
• Pulse Secure VPN server firmware version
• SSH keys for each server
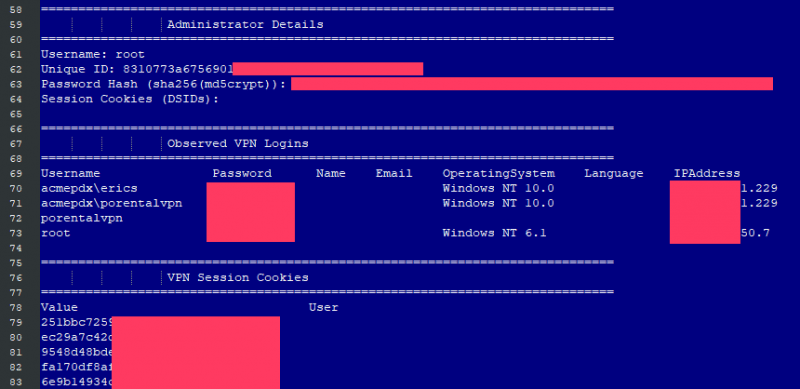
• A list of all local users and their password hashes
• Admin account details
• Last VPN logins (including usernames and cleartext passwords)
• VPN session cookies
Bank Security, a threat intelligence analyst specialized in financial crime and the one who spotted the list earlier today and shared it with ZDNet, made an interesting observation about the list and its content.
The security researcher noted that all the Pulse Secure VPN servers included in the list were running a firmware version vulnerable to the CVE-2019-11510 vulnerability.
Bank Security believes that the hacker who compiled this list scanned the entire internet IPv4 address space for Pulse Secure VPN servers, used an exploit for the CVE-2019-11510 vulnerability to gain access to systems, dump server details (including usernames and passwords), and then collected all the information in one central repository.
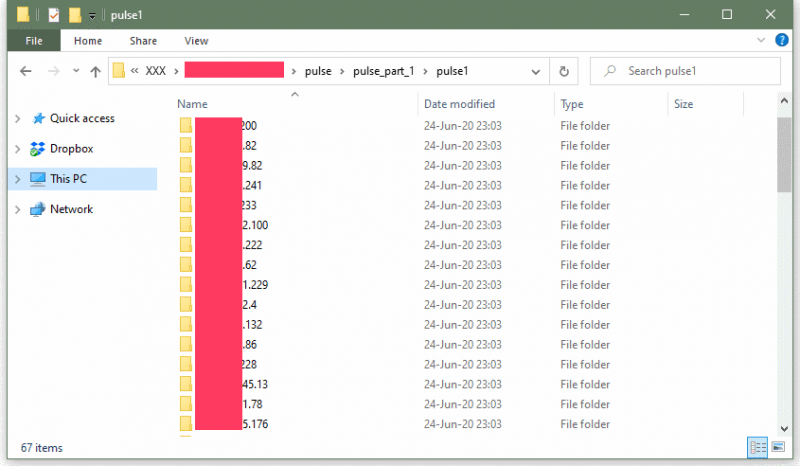
Based on timestamps in the list (a collection of folders), the dates of the scans, or the date the list was compiled, appear to between June 24 and July 8, 2020.
ZDNet has also reached out to Bad Packets, a US-based threat intelligence company that has been scanning the internet for vulnerable Pulse Secure VPN servers since August 2019, when the CVE-2019-11510 vulnerability was made public.
“Of the 913 unique IP addresses found in that dump, 677 were detected by Bad Packets CTI scans to be vulnerable to CVE-2019-11510 when the exploit was made public last year,” Bad Packets co-founder and chief research officer, told ZDNet today.
From the list, it appears that the 677 companies didn’t patch since Bad Packets’ first scan last year, and the June 2020 scans carried out by the hacker.
Even if those companies patch their Pulse Secure servers, they also need to change passwords to avoid hackers abusing the leaked credentials to take over devices and then spread to their internal networks.
This is very important, as Pulse Secure VPN servers are usually employed as access gateways into corporate networks so staff can connect remotely to internal apps from across the internet.
These types of devices, if compromised, can allow hackers easy access to a company’s entire internal network — hence the reason why APTs and ransomware gangs have targeted these systems in the past.
List shared on forum frequented by ransomware gangs
Making matters worse, the list has been shared on a hacker forum that is frequented by multiple ransomware gangs. For example, the REvil (Sodinokibi), NetWalker, Lockbit, Avaddon, Makop, and Exorcist ransomware gangs have threads on the same forum, and use it to recruit members (developers) and affiliates (customers).
Many of these gangs perform intrusions into corporate networks by leveraging network edge devices like Pulse Secure VPN servers, and then deploy their ransomware payload and demand huge ransom demands.
The publication of this list as a free download is a literal DEFCON 1 danger level for any company that has failed to patch its Pulse Secure VPN over the past year, as some of the ransomware gangs active on this forum are very likely to use the list for future attacks.
As Bank Security told ZDNet, companies have to patch their Pulse Secure VPNs and change passwords with the utmost urgency.
Source: ZDNet
- When Algorithms Manage Work under Economic, Legal and HR Perspectives. By Susana Taboas
- Brazil Sets Global Standard in Digital Identity with Child Protection Pact and 35 Million National ID Documents Issued
- Brazilian Tax Superplatform: The Global Benchmark for Digital Fiscal Innovation
- SEK adquiere Dreamlab Technologies Latam y refuerza su posición como actor clave de ciberseguridad en Chile y América Latina
- Gabriel Galípolo, president of the Central Bank, will be at the opening of Blockchain.RIO 2025
- Segura®Joins Locked Shields 2025, theWorld’s Largest Cyber Defense Exercise
- Brazil’s Ministry of Finance Wins Prestigious International Award for Study on Competition and Digital Platforms
- Brazilian Financial Regulator Announces Plan to Reform Crypto Tax Laws. Tim Alper – Cryptonews
- Researchers Uncover Nuclei Vulnerability Enabling Signature Bypass and Code Execution
- Are You Doing Digital Trust Right? By AET Europe – Part 2
Multi-cloud é o novo normal, mas é um desafio maior à segurança de dados
Industrial VPN Flaws Could Let Attackers Target Critical Infrastructures
Aplicativos VPN iOS fraudulentos tentam enganar usuários]
VPN apresenta riscos à segurança digital dos usuários
Nessa entrevista falamos sobre como as empresas estão enfrentando o grande desafio em atender as demandas de gerenciar a escala e complexidade crescentes dos ecossistemas de nuvem corporativa.
Os ambientes de tecnologia das organizações são acessados por todos os níveis hierárquicos da empresa, nos vários dispositivos que cada um possui, por meio dos mais variados tipos de acessos e em horários livres de controle. Como fazer o gerenciamento eficiente das identidades digitais nesse cenário complexo?
































