Writing advanced malware for a threat actor requires different groups of people with diverse technical expertise to put them all together. But can the code leave enough clues to reveal the person behind it?
To this effect, cybersecurity researchers on Friday detailed a new methodology to identify exploit authors that use their unique characteristics as a fingerprint to track down other exploits developed by them.
By deploying this technique, the researchers were able to link 16 Windows local privilege escalation (LPE) exploits to two zero-day sellers “Volodya” (previously called “BuggiCorp”) and “PlayBit” (or “luxor2008”).

Itay Cohen – Check Point Research 
Eyal Itkin – Check Point Research
“Instead of focusing on an entire malware and hunting for new samples of the malware family or actor, we wanted to offer another perspective and decided to concentrate on these few functions that were written by an exploit developer,” Check Point Research’s Itay Cohen and Eyal Itkin noted.
Fingerprinting an Exploit Writer’s Characteristics
The idea, in a nutshell, is to fingerprint an exploit for specific artifacts that can uniquely tie it to a developer. It could be in using hard-coded values, string names, or even how the code is organized and certain functions are implemented.
Check Point said their analysis began in response to a “complicated attack” against one of its customers when they encountered a 64-bit malware executable that exploited CVE-2019-0859 to gain elevated privileges.
Noticing the fact that the exploit and the malware were written by two different sets of people, the researchers used the binary’s properties as a unique hunting signature to find at least 11 other exploits developed by the same developer named “Volodya” (or “Volodimir”).
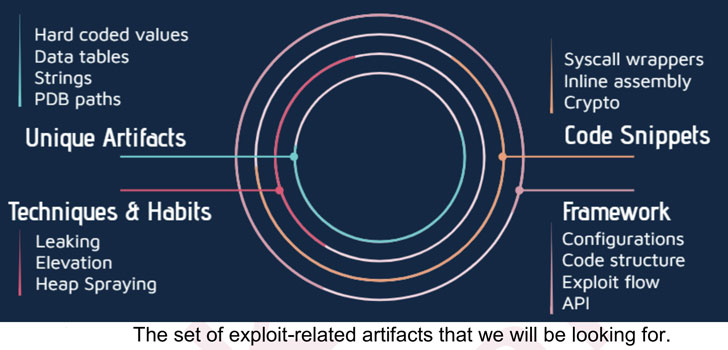
“Finding a vulnerability, and reliably exploiting it, will most probably be done by specific teams or individuals who specialize in a particular role. The malware developers for their part don’t really care how it works behind the scenes, they just want to integrate this [exploits] module and be done with it,” the researchers said.
Interestingly, Volodya — likely of Ukrainian origin — has been previously linked to selling Windows zero-days to cyberespionage groups and crimeware gangs for anywhere between $85,000 to $200,000.
Chief among them was an LPE exploit that leveraged a memory corruption in “NtUserSetWindowLongPtr” (CVE-2016-7255), which has been widely used by ransomware operators like GandCrab, Cerber, and Magniber. It’s now believed that Volodya advertised this LPE zero-day on the Exploit.in cybercrime forum in May 2016.
In all, five zero-day and six one-day exploits were identified as developed by Volodya over a period of 2015-2019. Subsequently, the same technique was employed to identify five more LPE exploits from another exploit writer known as PlayBit.
An Extensive Clientele and the Malware
Stating the exploit samples shared code level similarities to grant SYSTEM privileges to the desired process, the researchers said, “both of our actors were very consistent in their respective exploitation routines, each sticking to their favorite way.”
What’s more, Volodya also appears to have switched up his tactics during the intervening years, with the developer shifting from selling the exploits as embeddable source code in the malware to an external utility that accepts a specific API.
Besides ransomware groups, Volodya has been found to cater to an extensive clientele, including the Ursnif banking trojan, and APT groups such as Turla, APT28, and Buhtrap.
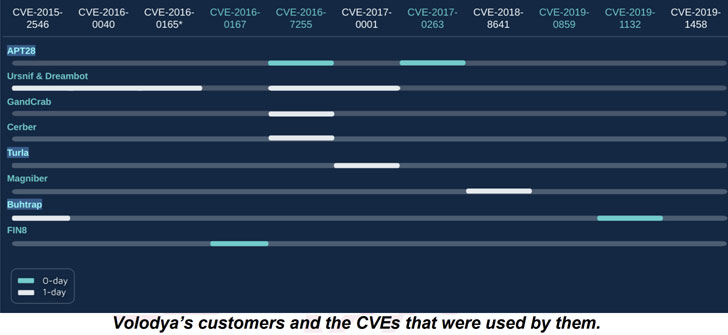
“The APT customers, Turla, APT28, and Buhtrap, are all commonly attributed to Russia and it is interesting to find that even these advanced groups purchase exploits instead of developing them in-house,” Check Point observed in its analysis.
“This is another point which further strengthens our hypothesis that the written exploits can be treated as a separate and distinct part of the malware.”
With cyberattacks expanding in scope, frequency, and magnitude, using an exploit developer’s code signature as a means to track down bad actors could provide valuable insight into the black exploit market.
“When Check Point finds a vulnerability, we demonstrate its severity, report it to the appropriate vendor, and make sure it’s patched, so it doesn’t pose a threat,” Cohen said.
“However, for individuals trading these exploits, it’s a completely different story. For them, finding the vulnerability is just the beginning. They need to reliably exploit it on as many versions as possible, in order to monetize it to a customer’s satisfaction.”
“This research provides insight into how that is achieved, and the buyers in this market, which often include nation-state actors. We believe that this research methodology can be used to identify additional exploit writers.”
- ITI publica Plano de Transformação Digital 2025-2027 com foco em biometria federal, assinatura eletrônica e interoperabilidade de dados
- Reino Unido inicia teste de Reconhecimento Facial ao Vivo – LFR em estações ferroviárias e inflama debate sobre vigilância e liberdades
- Tecnologia de Biometria ganha espaço como ferramenta estratégica de gestão educacional e prevenção a casos de violência em instituições de ensino
- IDV – Verificação de Identidade Digital em 2025: mercado, riscos e critérios de escolha de fornecedores
- Ação de saúde da mulher no Rio de Janeiro ganha reforço com biometria palmar da Biostation
Source: The hacker News
New Report Explains COVID-19’s Impact on Cybersecurity
How to manage your TLS certificates under Google’s new rules? Hear
































