Por Ademar Varela
O Touch ID, Fingerprints e outras tecnologias de digitalização e leitura de impressões digitais são implementações muito convenientes para os nossos smartphones, pois permitem que pagamentos sejam feitos mais rapidamente assim como o desbloqueio do dispositivo.
No entanto, Elliot Williams escreveu um artigo instigante explicando por que você nunca deve confiar no Touch ID em vez de usar uma senha no seu dispositivo, não importando o quão inconveniente isso possa ser.
Inicialmente, Williams reconhece que as senhas são terríveis e que nem todas são de fato seguras, mas tanto quanto nós temos um certo “ódio” em ficar digitando senhas, ele argumenta que depender de um toque de identificação para segurança móvel é uma opção muito pior. Há muitas razões para isso e um dos mais óbvios é que suas impressões digitais não é um segredo único que é difícil de encontrar.
“Você deixa suas impressões digitais em todos os lugares”, explica ele. “Elas podem ser apanhadas no papel, teclados e superfícies de mesa. Você não deixaria seu senha escrita em uma nota anexada ao seu monitor no trabalho, deixaria? Se o seu trabalho está usando sua impressão digital para autenticação, sua senha está, provavelmente, em seu monitor, agora. ”
E, claro, os hackers já têm mostrado que eles podem copiar as impressões digitais dos usuários usando vários métodos diferentes, incluindo scanear uma imagem de impressão digital de uma foto. Outros problemas com impressões digitais incluem o fato de que você não pode simplesmente redefini-las como você deseja redefinir uma senha comprometida.
Fonte: Linkedin
YOUR UNHASHABLE FINGERPRINTS SECURE NOTHING
Por Elliot Williams
Passwords are crap. Nobody picks good ones, when they do they re-use them across sites, and if you use even a trustworthy password manager, they’ll get hacked too. But you know what’s worse than a password? A fingerprint. Fingerprints have enough problems with them that they should never be used anywhere a password would be. 
Passwords are supposed to be secret, like the name of your childhood pet. In contrast, you carry your fingers around with you out in the open nearly everywhere you go. Passwords also need to be revocable. In the case that your password does get revealed, it’s great to be able to simply pick another one. You don’t want to have to revoke your fingers. Finally, and this is the kicker, you want your password to be hashable, in order to protect the password database itself from theft.
In the rest of the article, I’ll make each of these three cases, and hopefully convince you that using fingerprints in place of a password is even more broken than using a password in the first place. (You listening Apple andGoogle? No, I didn’t think you were.)
FINGERPRINTS ARE NOT SECRET
The first, and maybe most obvious, problem with using a fingerprint in place of a secret password is that they’re not secret at all. Think about the trope where the cops offer the bad guy a coffee in questioning and then subsequently take the mug down to the forensics lab to read his prints. Busted!
But it’s worse than that. You leave your fingerprints everywhere. They can be picked up off of paper, keyboards, and desk surfaces. You wouldn’t leave your password written down on a sticky-note attached to your monitor at work, would you? If your work is using your fingerprint for authentication, your password is probably on your monitor right now.
German hacker [Jan Krissler], who goes by [starbug], has been hammering this home every chance he gets. Back when the iPhone 5’s touchID system was just announced, [starbug] started salivating. He bought one immediately, played around with it for two days, and demonstrated that he could fake out the fingerprint reader before the lines around the block at the Apple Store had cleared. In this interview with Ars Technica, starbug complains that it was too easy. An unnamed Apple source said they’d expected it to take two months, not two days.
HOW TO MIMIC A FINGERPRINT
His technique to mimic a fingerprint is pretty simpel. He takes a copy of a fingerprint, then etches it into copper (as if making a PCB), coats the etching in graphite spray, and finally tops it all off with a layer of wood glue or latex. Where the copper was etched away, the glue-and-graphite finger mold is deeper, simulating the ridges on your finger. The graphite spray gives it the right bulk capacitance. Do this in skin-colored latex, and you’ve made something worthy of Mission Impossible for $5 in materials and one afternoon of your time. All you need is a good fingerprint image lifted from a mug or a book.
LIFT FINGERPRINTS FROM PHOTOS
 Don’t show your prints in pictures. [Starbug] reproduced the thumbprint of [Ursula von der Leyen], Germany’ Defense Minister, from a single photograph taken at a press conference. Whether the thumbprint is good enough to unlock the entire German army remains untested, but you get the point; hopefully they’re not using fingerprints for secret passwords.
Don’t show your prints in pictures. [Starbug] reproduced the thumbprint of [Ursula von der Leyen], Germany’ Defense Minister, from a single photograph taken at a press conference. Whether the thumbprint is good enough to unlock the entire German army remains untested, but you get the point; hopefully they’re not using fingerprints for secret passwords.
[Starbug] discusses the resolutions required and many more hacks against biometrics in general in this great talk at the Chaos Communication Congress (in German), but the point is that with enough resolution and/or a good enough lens, fingerprints can be taken from comfortable distances. The main limiting factors are depth-of-focus and lighting, which is bad news for politicians sitting on a well-lit stage in front a bunch of cameras. Politician or not, unless you’re always wearing gloves, your fingerprints are not good secrets.
FINGERPRINTS ARE NOT REVOCABLE
So let’s say that somehow your normal password gets leaked. How bad is it? In an ideal world, the website that has been hacked lets you know and tells you to change your password. You replace your dog’s name with your cat’s name, and the year of your birth with that of your kid sister’s. Problem solved!
But if your fingerprints are your password and they get leaked, it’s “impossible” to change them. Indeed in traditional fingerprint applications, uniqueness and immutability are the whole point — tying criminals to the scene of the crime, for instance. If you could just change your fingerprints after each heist, you wouldn’t have to wear those awkward gloves.
A fingerprint stays with you for life. Once I steal your fingerprint, I can unlock your current fingerprint-secured device and every fingerprint-secured device that you’ll ever buy in the future. Fingerprints are half-secrets that can’t ever be changed, and thus make lousy passwords. There’s not much more to say about this point, and it’s pretty damning, but it’s worth emphasizing because of the prevalence of bad policy out there.
For instance, sensitive government agencies have been using personal identity verification (PIV) cards that include a copy of the employee’s fingerprint. In addition to a correct password, federal employees subject to PIV have to swipe their finger, and the fingerprint is compared against the one stored in the card. The idea is to use the password and fingerprint match as a form of two-factor authentication.
And then the US Office of Personnel Management (OPM) got hacked and 5.6 million (!) fingerprints of government employees got taken, presumably by a foreign government’s spy agency. So now the Dept. of Homeland Security is possibly going to have to move to “three-factor authentication” because one of their factors is entirely burned. If the government had chosen a revocable second factor for the PIV cards, at least that part of the spill would be a lot easier to mop up.
Passwords need to be changed to remain secret and secure. Fingerprints don’t change.
FINGERPRINTS ARE NOT HASHABLE
The problem with fingerprints is that close is good enough, and needs to be. If I press my finger harder into one reader than into another, or swipe differently, or have a cut, I still want the reader to accept my fingerprint. Trained FBI agents make matches with “partials” all the time, and with reasonable accuracy. Close matches are a fact of life with human flesh and real-world scanners. But a fingerprint with a tiny flaw will hash into something entirely different from the reference version. What this means is that fingerprints are not hashable. Hashing makes passwords strong and without it, fingerprint protection is much weaker.
When a responsible website gets hacked these days, and the thieves walk away with the password database, they’re not actually in possession of a list of any passwords at all. Instead, what they get is a list of usernames andone-way hashes of the passwords. When you type your password in, the website hashes the result. If the trial hash matches the stored one, they can be sure that the password was right. Because the hash is essentially one-way, it’s exceptionally hard for anyone to start from the hashes and figure out what your password is. In fact, the easiest way to go from hashes back to passwords is to start guessing every possible password, compute its hash, and check for a match.
When you type your password in, the website hashes the result. If the trial hash matches the stored one, they can be sure that the password was right. Because the hash is essentially one-way, it’s exceptionally hard for anyone to start from the hashes and figure out what your password is. In fact, the easiest way to go from hashes back to passwords is to start guessing every possible password, compute its hash, and check for a match.
Contrast this with a naïve implementation where the website stores everyone’s passwords, but encrypts them with a master password. If the hacker can break the master password, he or she can decrypt the entire database and all of the passwords. And because this master password has to be used every time a normal password is validated, it’s going to be very vulnerable as well as very valuable. Encrypting each user’s data with a different master password just means that they’ve got to maintain a gigantic master password database, which doesn’t help things either. This is why every responsible website only stores hashes of users’ passwords.
Hashes can be made still better than encryption, though. If the security people are doing their job, the passwords are salted with something that’s different (but not necessarily secret) for each user before hashing; this slows down a brute-force mass-cracking attempt, because each person’s password is essentially hashed differently.
If you and I both use the password “!password123”, but my password has “elliot” added on the front and yours has “joe_user” our hashed values will differ. Once the hackers finally guess your password, because of the salt, they won’t automatically know mine.
And if the website’s security is really good, this hashing process will be repeated thousands of times with a slower algorithm which further slows down brute-force attacks. If it takes one half second to validate your login, it’s no big deal for you, but it’s a deal breaker for a brute-force attempt where they rely on millions of trials per second. As an example of best practices, the disclosure when the password manager LastPass got hacked is pretty solid. It’s still lousy that they got hacked, and you should still change your master password, but if it’s a good one nobody is going to be brute-forcing it any time soon.
Fingerprints and the Avalanche Effect
What does any of this have to do with fingerprints? Fingerprints don’t hash well, so all of the above security advantages of storing only salted, hashed passwords in the database don’t apply. That’s because in addition to being one-way, a good hash exhibits the avalanche effect: a small change in the password makes a much larger difference in the hash.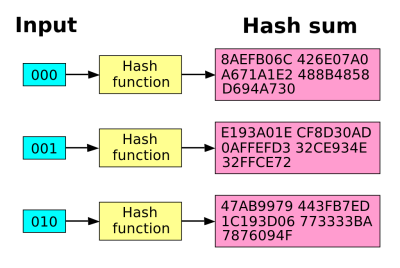
The string “!password123” hashed using the MD5 hashing function isb3a2efccbe10c39f2119979a6f9a3ab2, but “!Password123” isd2583f9c75fbc22890d39e7241927511. The two strings differ by one letter, the capitalized “P”, and yet the hashes are very different. This prevents the cracker, who is brute-forcing potential passwords to get a hash match, from knowing when he or she is getting close. If each correct letter in your password got the hash closer to the target hash, they’d guess it in no time. The avalanche effect means that guessing “close” to the password doesn’t help at all.
As I mentioned before, fingerprint technology needs to be “close enough”. A miss is as good as a mile once it’s hashed. Which means that fingerprints have to be stored in plaintext or encrypted but can’t usefully be hashed, because a good hash avalanches. Fingerprint databases are necessarily a weak link; anywhere your fingerprint is being stored, on your iPhone or PIV card or inside your electronic passport, there is a version of your fingerprint that someone could decrypt if they knew the master password.
Electronic Passports
A great example of hashing versus encryption is found in electronic passports. They contain an encrypted representation of your fingerprint and iris images because they’re considered to be sensitive information. But these can only be encrypted because the passport reader will need to be able to decrypt them to compare with your real fingers and eyes.
 On top of this, all of your non-sensitive information and the encrypted package are all hashed together, which makes it harder to tamper with any of the info without changing the hash. You might think you could tweak one bit here and apply an offsetting tweak there, but the avalanche effect foils that plan.
On top of this, all of your non-sensitive information and the encrypted package are all hashed together, which makes it harder to tamper with any of the info without changing the hash. You might think you could tweak one bit here and apply an offsetting tweak there, but the avalanche effect foils that plan.
At the end of the day, though, this means that the fingerprints on your passport are only secured from reading by encryption, and not a hash function. That’s fine for Customs because they only care that your fingerprint hasn’t been modified. For them your fingerprint is only really used to verify that you are you, and that’s hard to tamper with without breaking the hash that ties it to the rest of your information.
For privacy-minded individuals, on the other hand, it’s a bit more of a concern to have your fingerprints only encrypted. An evil-doer with your passport and the right password(s) could undo the encryption and get your fingerprints out. Although it’s probably easier to just lift your prints off the cover of the passport — fingerprints aren’t good secrets, remember?
CONCLUSION
Don’t use fingerprints as if they were passwords. Being permanent and relatively-easily verified and obtained makes them great for criminal investigations or for certifying that you are who you say you are. But they’re not passwords because they’re not secret, they’re not revocable, and they’re very difficult to store securely.


































