Cybercriminals not only steal credentials or infect computers with malware. They also hunt for users’ personal data, including passports and IDs, physical addresses, phone numbers and much more.
These cybercrimes can be classified as identity theft: utilizing the stolen data, crooks impersonate the victims to provide malicious activity. The perpetrators use a variety of cunning tricks to make users give away their data. Here’s the most recent example: an identity theft attack targeted 409 email addresses of universities and municipalities in the last decade of April.
The attackers used the email message below to lure the users:

The mail imitates a message from EL Cordo Lottery. In order to receive the prize, the email informs the receiver that they’re the lottery winner and asks to fill in a “Login Processing form” available through the link. The message itself is rather simple and obviously doesn’t look extremely enticing. But there are some interesting nuances about it.
The attackers used an e-mail of a well-known university department as the sender address (we don’t name the university here to protect the innocent). But in reality, the malicious message was sent from IP 189.72.174.152 that, as you can see below, belongs to The Secretariat of Public Security and Penitentiary Administration of Brasilia. This agency coordinates the activity of the public security forces in the country.
inetnum: 189.72.174.128/26
aut-num: AS8167.
abuse-c: CSIOI
owner: SECRETARIA DE SEG PÚB E ADMINISTRAÇÃO PENITENCIÁRI
ownerid: 01.409.606/0001-48
responsible: RODRIGO TAPIA PASSOS DE OLIVEIRA
owner-c: RTPOL
tech-c: RTPOL
created: 20171109
changed: 20171109
inetnum-up: 189.72.0.0/14
nic-hdl-br: RTPOL
person: Rodrigo Tapia Passos de Oliveira
created: 20130104
changed: 20130104
nic-hdl-br: CSIOI
person: CSIRT OI
created: 20140127
changed: 20140127
It’s hard to say precisely if whether the attacker is an employee of the Secretariat or the cybercriminals compromised the server of the organization. However, in both cases, Brazilian law enforcement definitely have valid reasons to investigate the situation.
Now, let’s find out what happens if a user takes the bait and clicks on the link.
As you can see, a form to fill in appears.

The form is was created by a legitimate Jotform service, which positioned itself as “the easiest way to create forms and collect data”, so we have here one more example of using legal services and tools for committing a crime. No doubt, this nuance also helps to lure the users. Many of them for sure would give away what the form requires: full name, physical address, email, phone number, date of birth, marital status and even a copy of the passport!


After seeing the graphics, you may be wondering: why do the perpetrators collect this information?
First, they can utilize the stolen data for an identity theft to cover their malicious activity. Identity theft is a crime when perpetrators impersonate a victim by using their private information. They can use it in various ways, to name a few: registering a website for illegal activity, opening a financial account for money laundering or drug selling, and impersonating the victim in state institutions or business companies etc.
Second, they can use this data to attack the victim in the future. They can prepare a spear-phishing attack based on the stolen data. Or even simply penetrate their house — why not, they’ve already got the victim’s physical address and a bunch of private information to make the penetration easier.
At the very least, they can just sell the data to other criminals in the Dark web.
However, cybercriminals are not the only ones hunting for personal data. Intelligence services of many countries also look for such information to provide cover for their agents in clandestine operations.
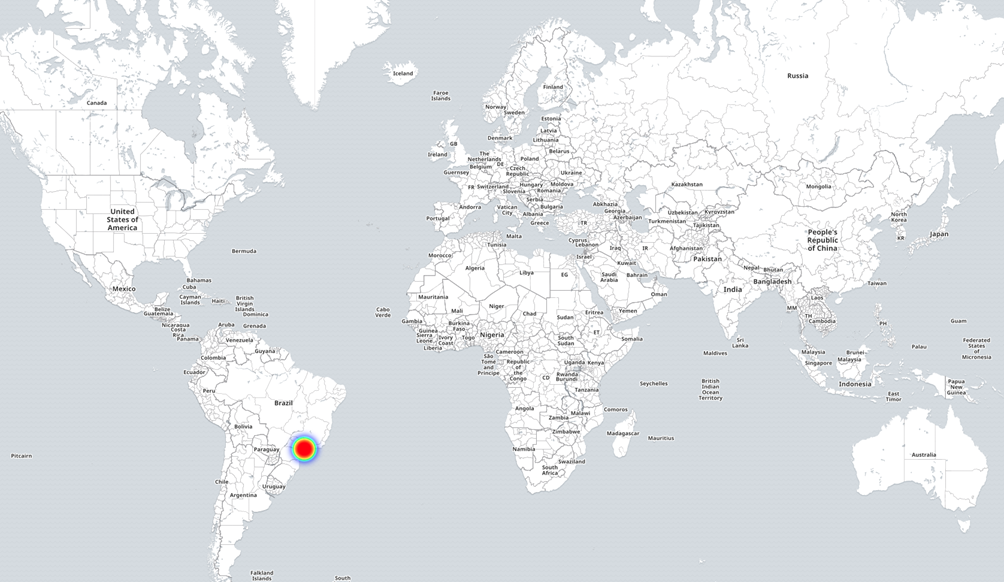
The attack started on April 20, 2018, at 07:39 UTC and ended on April 20, 2018, at 11:14 UTC. The attackers sent 409 emails, 392 of which were targeted to the email addresses of a few universities.

“Identity theft is a very dangerous cybercrime”, says Fatih Orhan, the Head of Comodo Threat Research Lab.
”Unfortunately, many people still underestimate it and easily give away their personal data. They don’t see any threat in filling in some questionnaire. Thus, for a cybercriminal to extract this information from a victim is even easier than make her download a malicious file. But the consequences of an identity theft may be no less disastrous than a malware infection. That’s why technical means of protection like Comodo KoruMail are especially helpful in such situations: they can identify the threat and neutralize it even before it reaches people. That just what happened in this case. The attack failed, the Comodo clients remained in safety”.