Cybersecurity researchers today unveiled a complex and targeted espionage attack on potential government sector victims in South East Asia that they believe was carried out by a sophisticated Chinese APT group at least since 2018
“The attack has a complex and complete arsenal of droppers, backdoors and other tools involving Chinoxy backdoor, PcShare RAT and FunnyDream backdoor binaries, with forensic artefacts pointing towards a sophisticated Chinese actor,” Bitdefender said in a new analysis shared with The Hacker News.
It’s worth noting that the FunnyDream campaign has been previously linked to high-profile government entities in Malaysia, Taiwan, and the Philippines, with a majority of victims located in Vietnam.
According to the researchers, not only around 200 machines exhibited attack indicators associated with the campaign, evidence points to the fact the threat actor may have compromised domain controllers on the victim’s network, allowing them to move laterally and potentially gain control of other systems.
The research has yielded little to no clues as to how the infection happened, although it’s suspected that the attackers employed social engineering lures to trick unwitting users into opening malicious files.
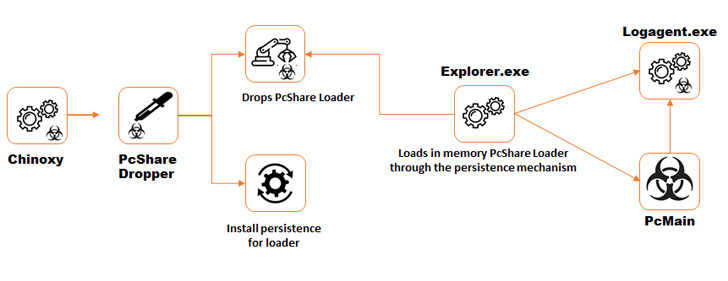
Upon gaining an initial foothold, multiple tools were found to be deployed on the infected system, including the Chinoxy backdoor to gain persistence as well as a Chinese remote access Trojan (RAT) called PcShare, a modified variant of the same tool available on GitHub.
Besides using command-line utilities such as tasklist.exe, ipconfig.exe, systeminfo.exe, and netstat to gather system information, a number of others — ccf32, FilePak, FilePakMonitor, ScreenCap, Keyrecord, and TcpBridge — were installed to collect files, capture screenshots, logging keystrokes, and exfiltrate the collected information to an attacker-controlled server.
The investigation also uncovered the use of the aforementioned FunnyDream backdoor starting in May 2019, which comes with multiple capabilities to amass user data, clean traces of malware deployment, thwart detection and execute malicious commands, the results of which were transmitted back to command-and-control (C&C) servers situated in Hong Kong, China, South Korea, and Vietnam.
“Attributing APT style attacks to a particular group or country can be extremely difficult, mostly because forensic artefacts can sometimes be planted intentionally, C&C infrastructure can reside anywhere in the world, and the tools used can be repurposed from other APT groups,” the researchers concluded.
“During this analysis, some forensic artifacts seem to suggest a Chinese-speaking APT group, as some of the resources found in several binaries had a language set to Chinese, and the Chinoxy backdoor used during the campaign is a Trojan known to have been used by Chinese-speaking threat actors.”
Source: The Hacker News
Digital Identity on the Blockchain: Securing User Data With Chainlink
Is quantum computing a cybersecurity threat?
The ultimate guide to encryption key management
- When Algorithms Manage Work under Economic, Legal and HR Perspectives. By Susana Taboas
- Brazil Sets Global Standard in Digital Identity with Child Protection Pact and 35 Million National ID Documents Issued
- Brazilian Tax Superplatform: The Global Benchmark for Digital Fiscal Innovation
- SEK adquiere Dreamlab Technologies Latam y refuerza su posición como actor clave de ciberseguridad en Chile y América Latina
- Gabriel Galípolo, president of the Central Bank, will be at the opening of Blockchain.RIO 2025
- Segura®Joins Locked Shields 2025, theWorld’s Largest Cyber Defense Exercise
- Brazil’s Ministry of Finance Wins Prestigious International Award for Study on Competition and Digital Platforms
- Brazilian Financial Regulator Announces Plan to Reform Crypto Tax Laws. Tim Alper – Cryptonews
- Researchers Uncover Nuclei Vulnerability Enabling Signature Bypass and Code Execution
- Are You Doing Digital Trust Right? By AET Europe – Part 2
- Are You Doing Digital Trust Right? By AET Europe – Part 1
- When do government agencies need to verify individuals (and what are their workflows)?
































